
A Report of Network Security Event provides a detailed account of incidents affecting the integrity, confidentiality, or availability of network resources. It includes critical information such as the nature of the threat, affected systems, timeline, and response measures taken. This report is essential for identifying vulnerabilities and enhancing future security protocols.
Network Security Incident Record
A Network Security Incident Record is a detailed document that captures all relevant information about a cybersecurity event. It includes data such as the time, nature, impact, and resolution of the incident. Maintaining accurate records helps organizations analyze threats and improve their security measures over time.
Cybersecurity Breach Summary
Cybersecurity breach summary provides a concise overview of unauthorized access incidents compromising sensitive data. It highlights the attack vectors, affected systems, and potential impacts on business operations. Timely summaries help organizations respond effectively and mitigate future risks.
Network Intrusion Detection Log
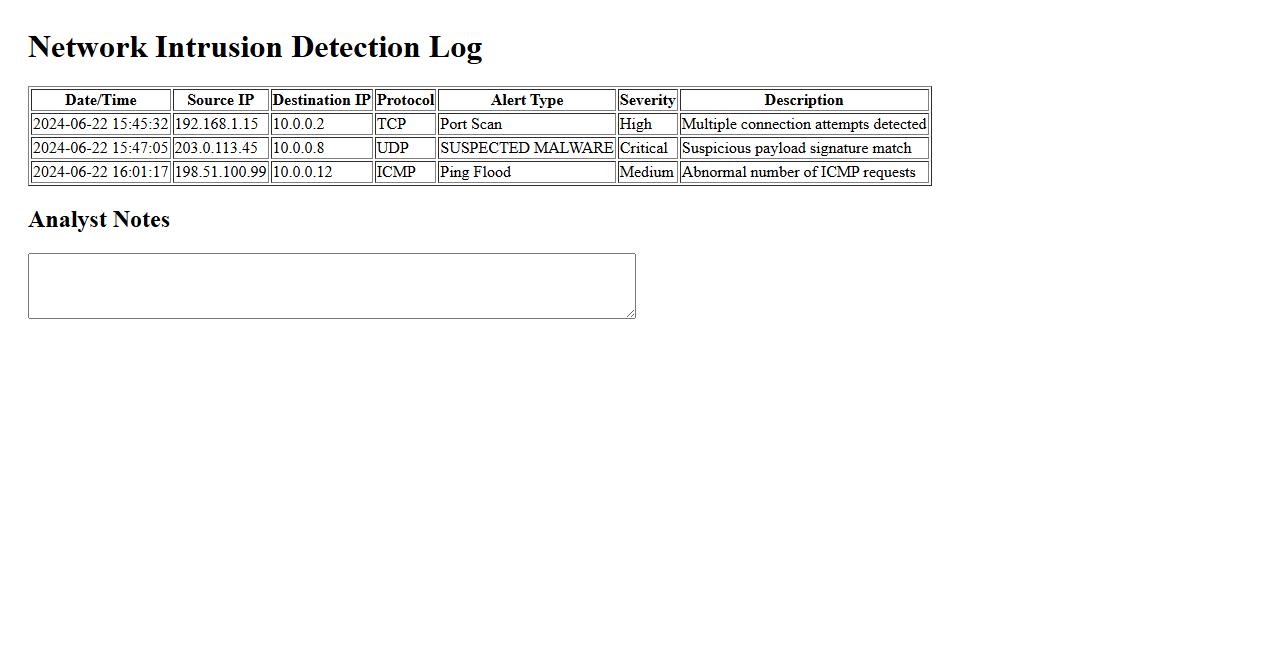
The Network Intrusion Detection Log records detailed information about potential security threats detected within a network. It helps administrators monitor unauthorized access attempts and analyze suspicious activities in real time. This log is essential for maintaining robust cybersecurity and preventing breaches.
Security Threat Assessment Report
The Security Threat Assessment Report provides a comprehensive analysis of potential risks and vulnerabilities within an organization. It identifies and evaluates threats to help implement effective security measures. This report is essential for enhancing an organization's overall safety and preparedness.
Unauthorized Access Incident Summary
The Unauthorized Access Incident Summary provides a concise overview of security breaches involving unauthorized entry into systems or data. It highlights the scope, impact, and response measures taken to mitigate risks. This summary is essential for understanding vulnerabilities and preventing future incidents.
Network Attack Response Documentation
Network Attack Response Documentation outlines the systematic procedures and protocols for identifying, analyzing, and mitigating network security breaches. It ensures a swift and organized reaction to cyber threats, minimizing downtime and damage. Properly maintained documentation empowers teams to respond effectively and enhance overall network resilience.
Information Security Event Analysis
Information Security Event Analysis involves the systematic examination of security incidents to identify potential threats and vulnerabilities. This process helps organizations detect, respond to, and mitigate cyber attacks effectively. By analyzing event data, companies can strengthen their overall security posture and prevent future breaches.
Network Compromise Investigation Report
The Network Compromise Investigation Report provides a detailed analysis of unauthorized access or breaches within a network. It outlines the methods used to detect, contain, and remediate the compromise, ensuring organizational security. This report helps stakeholders understand the impact and implement measures to prevent future incidents.
Security Vulnerability Incident Log
The Security Vulnerability Incident Log is a critical record that tracks all identified threats and breaches within a system. It helps organizations monitor, analyze, and respond to security incidents efficiently. Maintaining this log ensures timely detection and mitigation of potential risks.
Suspicious Activity Detection Summary
The Suspicious Activity Detection Summary provides an overview of identified unusual behaviors within a system. It highlights potential security threats by analyzing patterns and anomalies. This summary is essential for proactive threat management and ensuring data safety.
What is the primary objective of a Report of Network Security Event document?
The primary objective of a Report of Network Security Event is to provide a comprehensive record of any security incidents within a network. This document aims to facilitate prompt identification and mitigation of threats to safeguard the integrity and confidentiality of network data. Additionally, it serves as a basis for analyzing trends and improving future security measures.
Which key details must be included when documenting a network security incident?
When documenting a network security incident, it is essential to include the date and time of the event to track its occurrence accurately. The report must detail the nature of the incident, including affected systems, type of attack, and vulnerability exploited. Furthermore, it should record the immediate actions taken and any evidence collected to aid in further investigation.
How does the report categorize different types of network security events?
The report categorizes network security events based on the severity and type of the incident, such as malware, unauthorized access, or denial-of-service attacks. Each category helps prioritize response efforts and resource allocation effectively. Categorization also aids in identifying patterns and improving threat detection mechanisms.
What methodologies does the report use to assess the impact of a security event?
The report employs methodologies such as risk assessment and impact analysis to evaluate the consequences of a security event. It considers factors like data loss, system downtime, and potential financial repercussions. These assessments guide decision-making for recovery strategies and future prevention protocols.
Which stakeholders are identified as recipients or reviewers of the network security event report?
Key stakeholders receiving the network security event report include IT security teams, management, and compliance officers. These groups ensure that appropriate actions are taken and that the organization remains compliant with regulatory requirements. Additionally, external auditors or law enforcement may be involved depending on the severity of the incident.
